Certificate based rapid authentication provides a strong, secure and extremely fast endpoint authentication mechanism. It uses your corporate PKI (Public Key Infrastructure) to provide immediate, authenticated network access for corporate users and other known endpoints. Oct 05, 2015 The full command line for uninstalling Forescout SecureConnector is wscript.exe 'C: Windows Options Packages ForescoutSecureConnector3.702x86V04 UninstallForescoutSecureConnector3.702x86V04.vbs' /B. Keep in mind that if you will type this command in Start / Run Note you might get a notification for administrator rights.
ForeScout, a multi-award winning automated network security platform, gives you real-time visibility and control over everything connecting to your network; all devices, all operating systems, all applications, all users. Turbotax premier 2014 mac download.
A powerful auditing tool CounterACT monitors every device, it’s operating system and version, MAC & IP, whether its been on the network for a few minutes or all day. ForeScout also acts as an integration tool (using their ControlFabric technology) for your AV, next generation firewall and IDS products, allowing automated interoperability as key security tools share information to provide a complete network defence strategy.
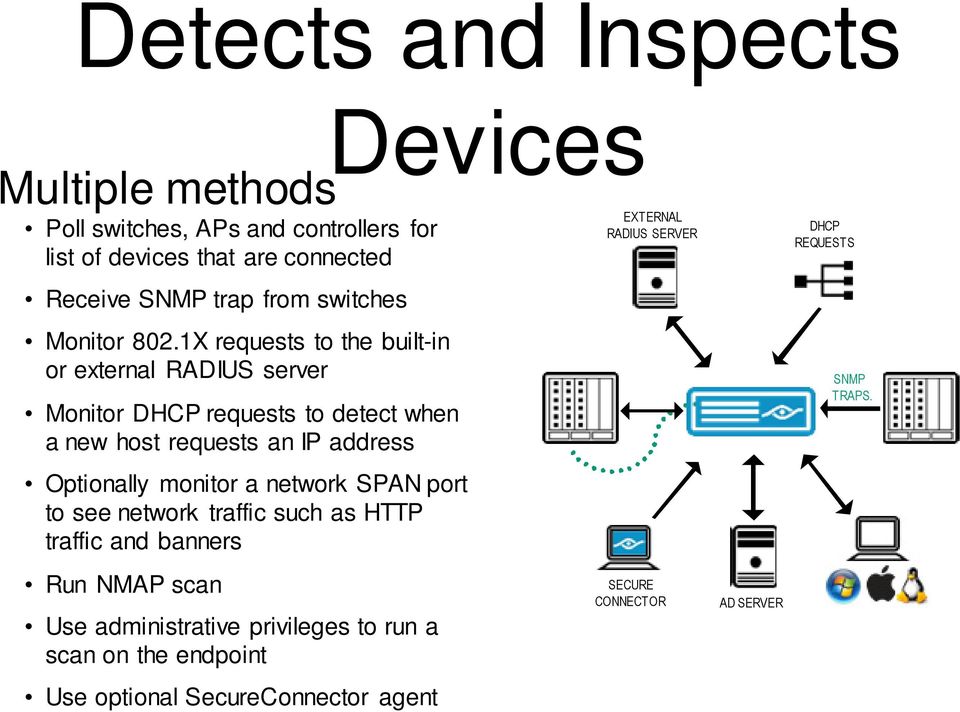
ForeScout CounterACT is easy to install because it requires no software, no agents, no hardware upgrades or reconfigurations. Everything is contained within a single appliance or virtual appliance.
Named as a Leader by Gartner, ForeScout offers real time threat mitigation, can grant or block access onto the network via automated policies and integrates with existing security tools such as McAfee, Palo Alto, FireEye and many more to bridge remediation.
ForeScout can help with:
- End Point Compliance – Audit for all connected devices, know what’s on your network without your knowledge, sometimes without proper security controls. Perhaps you need visibility of XP devices or to pass code of connection for access to the Public Services Network.
- Non-corporate devices – When guests, contractors or staff bring their own device to your location, they need to remain productive, perhaps access the Internet or additional resources, but their access must be limited without risk of malware or compliance breach.
- Rogue devices – Well-meaning employees can extend your network with inexpensive wiring hubs and wireless access points. These devices can cause your network to become unstable, and they can be a source of infection and data loss.
- Malware and botnets – Studies show that even well-managed enterprises have infected computers because of zero-day attacks and/or out-of-date antivirus. AV can only update the devices it knows about.
- ForeScout ControlFabric – a set of technologies that enables ForeScout CounterACT and other IT solutions to exchange information and efficiently mitigate a wide variety of network, security and operational issues. As a result, you can squeeze higher utilization from your existing security investments, efficiently pre-empt and contain exposures, and enhance your overall security.
In a recent independent survey 93% of current owners indicated the product met or overwhelmingly exceeded their ROI requirements and 94% stated they were likely to recommend it.
To arrange a discussion with one of our engineers call us now on 01677 428700 or email info@fullcontrolnetworks.co.uk, alternatively you can see it on the manufacturer’s website.
Key Features
- Integrated appliance. ForeScout CounterACT includes everything in a single appliance. No software to install, nothing to configure. Built-in integration lets you leverage your existing infrastructure including directory, switches, endpoint security systems, patch management systems, ticketing systems and reporting systems.
- 802.1x or not. ForeScout CounterACT can utilize 802.1x for authentication and switch control. Or, you can avoid the limitations of 802.1x and use ForeScout’s alternative technologies. The choice is yours.
- Visibility. ForeScout CounterACT’s Asset Inventory provides real-time, multi-dimensional network visibility and control, allowing you to track and control users, applications, processes, ports, external devices, and more.
- Guest registration. ForeScout CounterACT’s automated process allows guests to access your network without compromising your internal network security. ForeScout CounterACT includes several guest registration options allowing you tailor the guest admission process to your organization’s needs.
- Real-time mobile device control. ForeScout CounterACT detects and controls hand-held mobile devices connected to your Wi-Fi network. Supports iPhone/iPad, Blackberry, Android, Windows Mobile and Nokia Symbian.
- Threat detection. ForeScout CounterACT includes ActiveResponse™, a patented threat detection engine which monitors the behavior of devices post-connection. ActiveResponse blocks zero-day self-propagating threats and other types of malicious behavior. Unlike other approaches, ActiveResponse does not rely on signature updates to remain effective, which translates to low management cost.
- Rogue device detection. ForeScout CounterACT can detect rogue infrastructure such as unauthorized switches and wireless access points by identifying whether the device is a NAT device, identifying whether the device is on a list of authorized devices, or identifying situations where a switch port has multiple hosts connected to it.
- Role-based access control. ForeScout CounterACT ensures that only the right people with the right devices gain access to the right network resources. ForeScout leverages your existing directory where you assign roles to user identities.
- Flexible Control Options. Unlike early generation NAC products that employed heavy-handed controls and disrupted users, ForeScout CounterACT provides a full spectrum of enforcement options that let you tailor the response to the situation. Low-risk violations can be dealt with by sending the end-user a notice and/or automatically remediating his security problem; this allows the user to continue to remain productive while remediation takes place.
- Policy Management. ForeScout CounterACT lets you create security policies that are right for your enterprise. Configuration and administration is fast and easy thanks to ForeScout CounterACT’s built-in policy wizard and knowledge base of device classifications, rules and reports.
- Out-of-band deployment. ForeScout CounterACT deploys out-of-band which eliminates issues regarding latency and potential points of failure in your network.
- Scalability. ForeScout CounterACT has been proven in customer networks exceeding 250,000 endpoints. ForeScout CounterACT appliances are available in a range of sizes to accommodate networks of all sizes.
- Clientless operation. Since ForeScout CounterACT is a clientless solution, it works with all type of endpoints–managed and unmanaged, known and unknown. Nothing escapes ForeScout CounterACT. If it’s on your network, ForeScout CounterACT sees it.
- Optional client. ForeScout CounterACT gives you the option to install either a persistent or a dissolvable lightweight client, giving you additional control over the endpoint. Client supports Windows, Mac and Linux and can be automatically deployed when the user connects to the network and registers their identity on the system.
- IT infrastructure integration. Unlike proprietary NAC products, ForeScout CounterACT is fast and easy to install because it supports an extensive range of third-party networking and security hardware and software, including both 802.1x and non-802.1x enterprise switches.
- Authentication. ForeScout CounterACT supports existing standards-based authentication and directories such as 802.1x, LDAP, RADIUS, Active Directory, Oracle and Sun.
- Reporting. ForeScout CounterACT has a fully integrated reporting engine that helps you monitor your level of policy compliance, fulfill regulatory audit requirements, and produce real-time inventory reports.
- Endpoint compliance. ForeScout CounterACT can ensure that every endpoint on your network is compliant with your antivirus policy, is properly patched, and is free of illegitimate software such as P2P.
Product in Detail
ForeScout CounterACT is an automated security control platform that delivers real-time visibility and control of all devices on your network. ForeScout CounterACT automatically identifies who and what is on your network, controls access to your network, measures compliance with your security policies, blocks network threats, and remediates endpoint security violations when they occur. CounterACT makes you smarter, your network more secure, and your staff less busy by automating tasks that are currently laborious. Add in the collaberation with your existing security tools, such as McAfee, Palo alto, FireEye, Mobile Iron and lots more using their Extended Modules, which allow interoperability and the reassurance of complete network security.
Network Access Control
Forescout Agent Removal

ForeScout CounterACT for Network Access Control enables employee, guest and contractor access your network – wherever, however and whenever – without compromising your security. CounterACT integrates with your current network, security and identity infrastructure to assure the right users and their devices gain appropriate access. Leveraging built-in policy templates, CounterACT can automatically manage employee and guest access in a way that is seamless for those that comply and automated for those that don’t. CounterACT is the most superior NAC solution on the market.
Endpoint Compliance
Forescout Client Download
ForeScout CounterACT for Endpoint Compliance automatically enforces security policies for everyone and everything on your network, which helps you minimize your security risks. Because ForeScout CounterACT is agentless, it works with all type of endpoints–managed and unmanaged, known and unknown, physical, mobile and virtual. CounterACT can discover security weaknesses with your existing agent-based security systems that would otherwise go undetected. Literally, CounterACT can find and fix endpoint violations without IT intervention – saving your organization considerable time, resources and money. Smart mac address changer download.
What Is Forescout Software
Threat Prevention
ForeScout’s patented ActiveResponse™ technology is included in every product that we sell. ForeScout ActiveResponse blocks both known and unknown attacks with 100% accuracy. This unique technology does not require signature updates, nor suffers from false positives. And since operates with zero maintenance, you automatically gain real-time protection inside your network in full blocking mode. ForeScout CounterACT provided zero-day protection against Conficker, Zeus and Stuxnet.
Regulatory Compliance and Audit Reports
ForeScout CounterACT gives you real-time endpoint intelligence and security posture awareness. Our platform integrates with leading network, security, host-based security system (HBSS) and identity platforms to support compliance mandates. In addition, CounterACT supports the leading security information event management (SIEM) systems to provide endpoint configuration details, correlate access and compliance violations, and expedite incident response. Within CounterACT, the built-in report templates helps organizations monitor policy compliance levels, support regulatory audit requirements, and produce real-time inventory reports. As a result, CounterACT effectuates GRC initiatives and reduces auditing processes.
Mobile Security
ForeScout CounterACT for Mobile Security provides real-time visibility and control for smartphones, tablets, netbooks and other corporate and personal mobile devices connected to your network. Our solution complements/enables Wireless Access Points (WAP), Virtual Device Interface (VDI), Mobile Enterprise Application Platforms (MEAP) and Mobile Device Management (MDM) approaches. CounterACT can automatically identify and fingerprint managed and personal mobile devices, facility employees or guests using multiple devices, can eliminate rogue WAP, and identify malicious network activity. With CounterACT for Mobile Security, you can let users enjoy the productivity benefits of modern handhelds while you protect your network against data loss and malicious threats.
Forescout Secure Connector Mac Download Cnet
The ForeScout Difference
Forescout Secure Connector Mac Download Windows 10
ForeScout CounterACT is dramatically easier and faster to deploy than traditional policy enforcement products. Here is why:
Forescout Secure Connector Mac Download Google Chrome
- One box, one day to install: Everything is contained in a single physical or virtual appliance. Setup is easy with built-in configuration wizards:
- ForeScout works with what you have: All your existing switches, routers, firewalls, endpoints, patch management systems, antivirus systems, directories, ticketing systems–ForeScout CounterACT works with them. We require no infrastructure changes or equipment upgrades.
- No software: ForeScout CounterACT is agentless, which means it works with all types of endpoints–managed and unmanaged, known and unknown, authorized and rogue. No client installation is required.
- Non-disruptive: Unlike first generation NAC products that immediately disrupt users with heavy-handed access controls, ForeScout CounterACT can be deployed in a phased approach which minimizes disruption and accelerates results. In the initial phase, CounterACT gives you visibility to your trouble spots. When you want to move forward with automated control, you can do so gradually, starting with the most problematic locations and choosing an appropriate enforcement action.
- Accelerated results: ForeScout CounterACT provides useful results on Day 1 by giving you visibility to problems on your network. The built-in knowledge base helps you configure security policies quickly and accurately.



